Product Center
4009-610-038
Contact Us
Location:Home > Product Center >Detection of defensive >
Green alliance Information Security and defense competitive platform Information Security Competition System (ISCS), is a contestant, network Security theory knowledge and practical problems handling capacity of Competition.
advantage
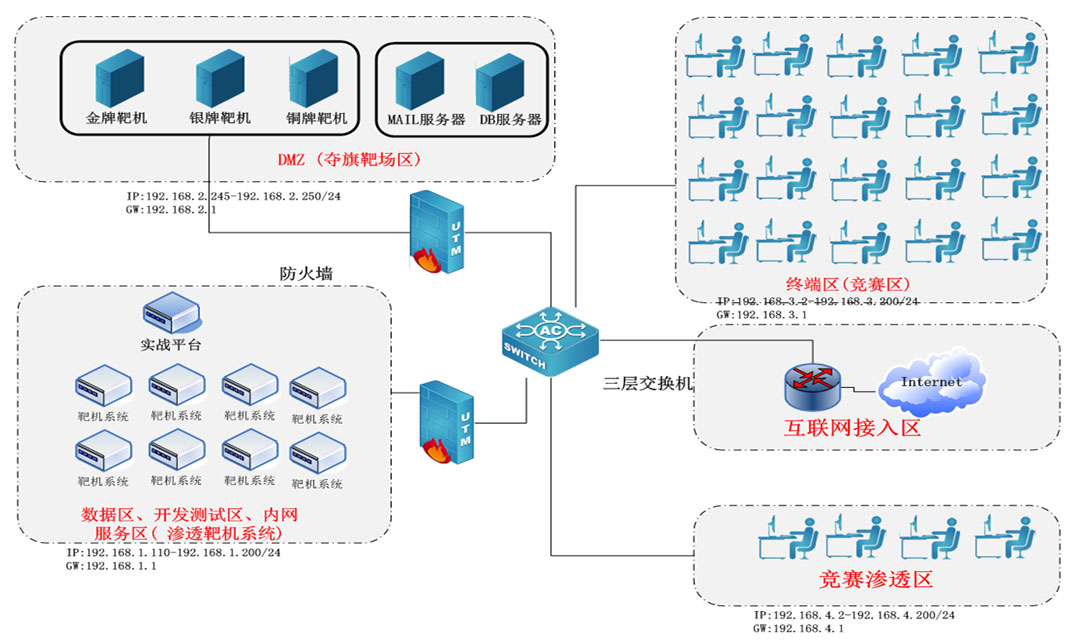
The core technology
Cloud laboratory techniques
Through a variety of means, such as virtual machine technology, but on the ISCS for remote participants to provide a complete set of offensive and defensive drills environment, remote participants completed only through a web browser can convenient remote all security defense experiments, the actual network running environment or equipment will not cause any harm.
Attack-defense environment experiment technology
About a suppositional environment needed for the test all components, including tools, running environment, main service program, non-public technical documentation such as through the experiment of encryption technology to form a complete package, can be easily managed and load. Using experimental package snapshot technology teachers can facilitate the students' test score.
Virtualization technology
In the main operating system on different virtual servers, virtual each application layer in the experimental program is running in the independent software environment, start many safety experiments at the same time, the use of system resources utilization, improve equipment performance.
广东大中信息技术有限公司 Powered by hunuo.com 粤ICP备18106562号-1
