Product Center
4009-610-038
Contact Us
Location:Home > Product Center >Detection of defensive >
In recent years, frequent user to leak sensitive information, to the enterprise reputation and economy brought huge losses; And events of the prism door, pose a threat to national security. This makes the country at the policy level, enterprises in consciousness, to sensitive information leakage protection, and security products independently controllable unprecedented strict requirements are put forward. Green unita in security industry for many years accumulation, timely introduced a completely independent research and development of green au Data leakage protection System (NSFOCUS Data Loss Prevention System, hereinafter referred to as NSFOCUS DLP).
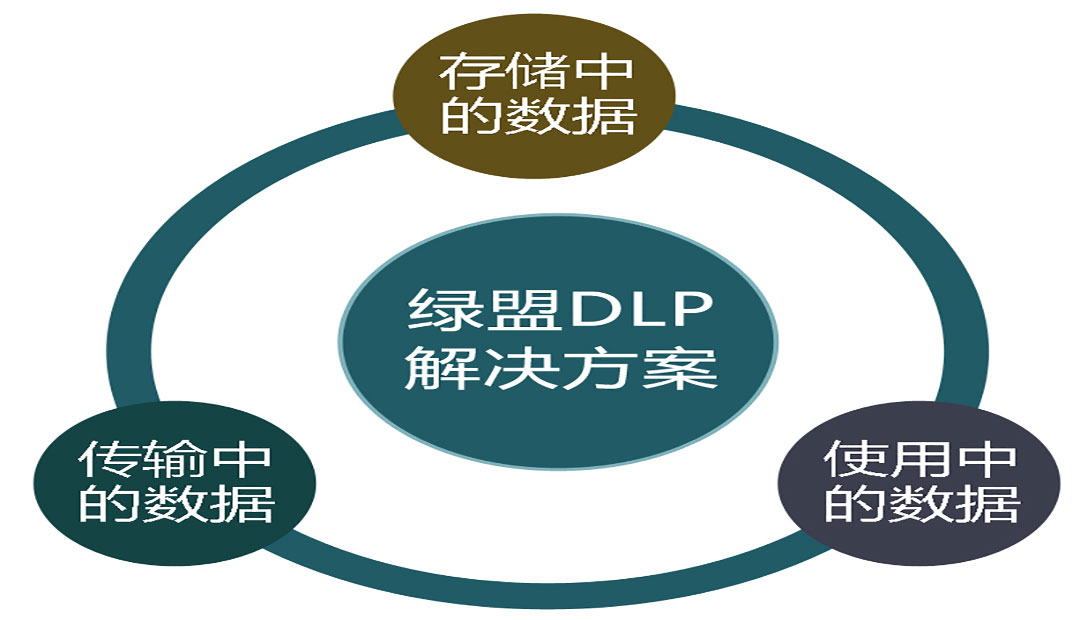
Customer value
1, meet compliance requirements
It can help users meet specification and SOX, such as PCIDSS and other information security regulatory requirements.
2, found that sensitive data
Found that sensitive data storage distribution and safe state, regulation to ensure users to provide a solid foundation.
3, prevent data leakage
To advance to sensitive data, the comprehensive integration of leak protection approaches, protect sensitive data is not lost.
4, traces the leak
Comprehensive logging, let the leaks can check can investigate, improve enterprise data security management capabilities.
Product advantage
Complete protection system: set prior scan, matter identification and afterwards back into an organic whole, in view of the three forms of data lifecycle (storage, use and transport), create integration protection ability.
Scanning: comprehensive advance quickly found huge amounts of sensitive data in the enterprise network distribution, provide the basis for enterprise security decisions, such as construction provides the basis.
Efficient recognition engine: based on Chinese semantic recognition engine, precise detection algorithm, rule configuration agile diversity, can be for a variety of data types, document coding is used to identify the depth of the sensitive information
Intensive processing strategy: in addition to the normal processing means such as records, intercept, alarm, more can be forced to sensitive data encryption, so as to provide a more intensive leak protection.
Leading local design: on the application of the local Chinese comprehensive monitoring protection, such as QQ, 163 mailbox, weibo, etc; Leading Chinese semantic recognition engine, support complex Chinese semantic and context sensitive information identification.
Key features
Data can provide key data, regular, fingerprint identification technology, to recognize the Word/EXCEL/PowerPoint/PDF/TXT/RAR/ZIP / 7 z/GZ multiple formats and the formatted document format.
Data classification support to the remote server, terminal equipment scanning and sensitive information classification, anytime and anywhere find sensitive data distribution and data security status.
Terminal protection support to intercept sensitive data through the terminal peripherals interface (such as U disk copy, print, burn, infrared, bluetooth, etc.), as well as common applications (such as chat, mail client, etc.) for transmission of leaks.
Network protection protocol analysis technology comprehensively and accurately, to support the transmission of sensitive data through the network monitoring and protection (e.g., network backup, weibo, FTP, BBS, etc.).
Email protection support is sensitive to enterprise email recognition (such as text, titles, accept the sender, accessories, etc.), prevent leakage sensitive data by E-mail.
Audit report provides logging, statistics, and other functions, to achieve security status quo can be controlled, leaks the traceability, the security situation can be measured.
广东大中信息技术有限公司 Powered by hunuo.com 粤ICP备18106562号-1
